Incorrect
The question refers to one of the common scenarios for temporary credentials in AWS. Temporary credentials are useful in scenarios that involve identity federation, delegation, cross-account access, and IAM roles. In this example, it is called enterprise identity federation considering that you also need to set up a single sign-on (SSO) capability.
The correct answers are:
– Setup a Federation proxy or an Identity provider
– Setup an AWS Security Token Service to generate temporary tokens
– Configure an IAM role and an IAM Policy to access the bucket.
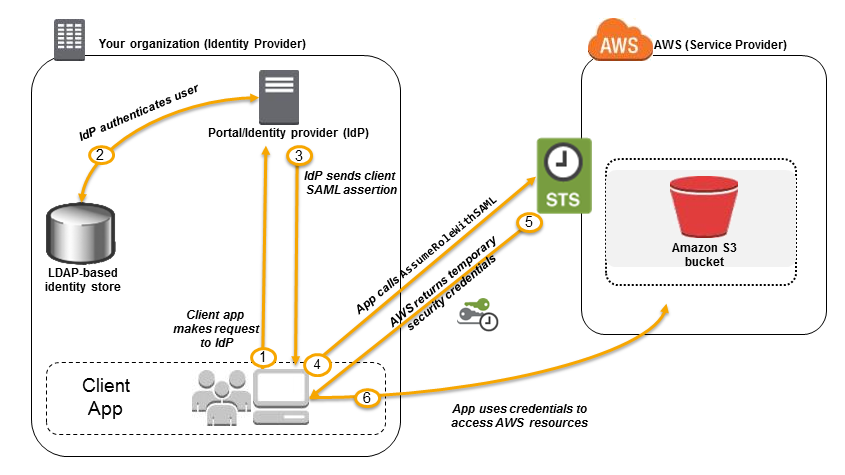
In an enterprise identity federation, you can authenticate users in your organization’s network, and then provide those users access to AWS without creating new AWS identities for them and requiring them to sign in with a separate user name and password. This is known as the single sign-on (SSO) approach to temporary access. AWS STS supports open standards like Security Assertion Markup Language (SAML) 2.0, with which you can use Microsoft AD FS to leverage your Microsoft Active Directory. You can also use SAML 2.0 to manage your own solution for federating user identities.
Using 3rd party Single Sign-On solutions such as Atlassian Crowd, OKTA, OneLogin and many others is incorrect since you don’t have to use 3rd party solutions to provide the access. AWS already provides the necessary tools that you can use in this situation.
Mapping each individual user to a designated user folder in S3 using Amazon WorkDocs to access their personal documents is incorrect as there is no direct way of integrating Amazon S3 with Amazon WorkDocs for this particular scenario. Amazon WorkDocs is simply a fully managed, secure content creation, storage, and collaboration service. With Amazon WorkDocs, you can easily create, edit, and share content. And because it’s stored centrally on AWS, you can access it from anywhere on any device.
Setting up a matching IAM user for each of the 1200 users in your corporate directory that needs access to a folder in the S3 bucket is incorrect since creating that many IAM users would be unnecessary. Also, you want the account to integrate with your AD or LDAP directory, hence, IAM Users does not fit these criteria.
References:
https://docs.aws.amazon.com/IAM/latest/UserGuide/id_roles_providers_saml.html
https://docs.aws.amazon.com/IAM/latest/UserGuide/id_roles_providers_oidc.html
https://aws.amazon.com/premiumsupport/knowledge-center/iam-s3-user-specific-folder/
IAM 정책을 사용하여 사용자별 폴더에 대한 액세스 권한 부여
IAM 정책을 사용하여 특정 S3 폴더에 대한 사용자별 액세스 권한을 부여하려면 어떻게 해야 합니까? 최종 업데이트 날짜: 2021년 10월 5일 IAM 사용자 정책을 사용하여 Amazon Simple Storage Service(Amazon S3)
aws.amazon.com
근데 지금 보니까 aws internal network로 들어가면 SSO 먹히던데... 이게 그거인가봄.
'CLOUD > AWS Cloud' 카테고리의 다른 글
| Gateway Load Balancer (0) | 2022.10.29 |
|---|---|
| EBS, EBS snapshot (0) | 2022.10.29 |
| AWS network cidr (0) | 2022.10.27 |
| AWS Network Firewall (0) | 2022.10.27 |
| Networking cost in AWS network (0) | 2022.10.27 |